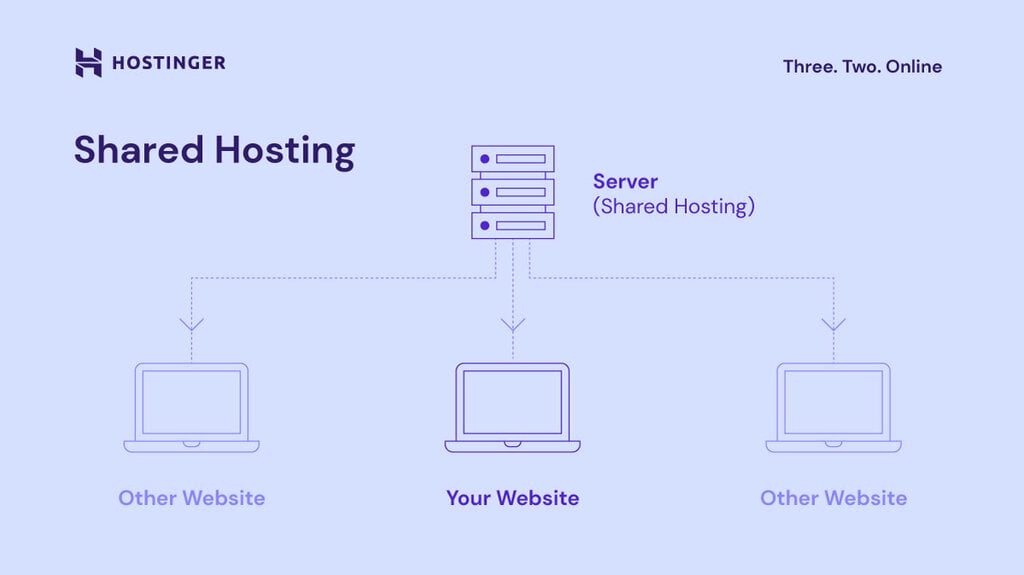
The 9-Second Trick For Cyber Security Training

Ransomware assaults target numerous different types of weaknesses in your organizations defences. One of your most vital defences you can have are your employees. You need to try to proactively concentrate on creating customized cyber safety training for your workers. This will aid users avoid cyber occurrences and also reinforce cyber safety and security in the workplace.
The significance of cybersecurity in this considerably internet-centered globe is supreme. To comprehend what cyber security is and its relevance, you can look for specialized IT Security accreditations online. These training courses will certainly upgrade your intuitive abilities and also allow you to involve with specialists in the sector. Cybersecurity is the practice of safeguarding electronic info by alleviating details risks and susceptabilities.
The value of cybersecurity in the digital globe is tremendous. Cyber Security Training. As our dependancy on modern technology grows, so does our vulnerability to these strikes. Cybersecurity aids to protect our information and systems from these hazards.
Rumored Buzz on Cyber Security Training
Cyber safety is important for students due to the fact that they usually target online assaults. In a recent case, a group of students from an university in the USA was targeted by hackers who got access to their individual details, including their Social Safety numbers and bank card info. Cyber Security Training. The cyberpunks then used this information to fraudulently bill hundreds of dollars to the students' bank card.
This case highlights the relevance of cyber safety and security for pupils, that are commonly the targets of cybercrime. If a trainee's personal details is swiped in a cyber assault, it can be utilized to commit identification burglary. It can wreck the student's credit history, making it hard for the pupil to obtain finances for university or a cars and truck.
The importance of Cyber Safety and security for services as well as companies can be seen when it comes to the target data breach. In this instance, cyberpunks were able to access to the target's customer data, consisting of credit report and also debit card info. It caused target having to pay out numerous dollars in problems as well as losing customer count on.
Cyber Security Training - Truths
One more information violation instance would certainly be the Wan na, Cry ransomware strike, which targeted services and also companies worldwide. This attack caused the loss of information and cash for lots of companies, as well as some were also required to close down. certified Honest Hacking programs for people to work towards securing information from violations and malware.
If this data had come under the wrong hands, it could have been utilized for identification burglary, fraud, or other malicious functions. Recently, there have been several prominent cyberattacks that have had a damaging effect on businesses and also people. These are burglary of social protection numbers, savings account information, credit score card information, as well as delicate information leakages.
These strikes have actually highlighted the relevance of having solid cybersecurity procedures in position. A few of the most common cyberattacks include: Phishing is a kind of cyberattack that entails tricking individuals into clicking harmful web links or accessories. It can cause the burglary of delicate information, such as login qualifications or monetary information.
The Best Guide To Cyber Security Training
It can swipe information, hijack tools, or launch strikes on various other systems. A denial-of-service strike is a sort of assault that prevents customers from accessing a system or service (Cyber Security Training). This can be done by swamping the system with website traffic or requests or harming it so it can no much longer work appropriately.

This is necessary because it enables business to keep a competitive benefit and also maintain their services and products secure from competitors. Additionally, it helps to ensure that brand-new products as well as services are not easily replicated or taken why not look here before they her comment is here can be released to the marketplace. The cloud has actually changed just how we think of IT, yet it has actually also presented brand-new security risks.
Everything about Cyber Security Training
This agility can also introduce brand-new security dangers. A cloud provider may not have the exact same security controls as a traditional on-premises information.
They must deal with their cloud providers to make sure that ample security controls remain in location. They need to likewise consider utilizing a cloud safety and security platform to help manage and also monitor their cloud atmosphere. The web has actually ended up being a staple in service procedures for the bulk of business around the world.
By taking these steps, businesses can reveal their commitment to shielding consumer and worker information, which can help to develop as well as keep trust. The importance of cybersecurity to make sure an organization's monetary placement can not be downplayed. In today's interconnected globe, where sensitive information is usually kept electronically, a breach in safety and security can have dreadful effects.
The Buzz on Cyber Security Training
An additional essential facet of cybersecurity is employee training. Staff members must be trained on just how to spot possible cyber risks and what to do if they come across one.
You must routinely monitor your network for any kind of suspicious activity. If you over here take these steps, you will significantly reduce the possibilities of your organization coming to be a sufferer of cybercrime. There are lots of reasons that people require to safeguard their information. One reason is that if data is not covered, unauthorized people can access and also use it.